Leveraging Microsoft's cloud-native XDR technologies, our service provides round-the-clock threat monitoring, giving you peace of mind knowing that your organization is watched closely after cyber threats. With our MDR service, we aim to detect and respond to threats in real time, minimizing the impact of any potential breaches. Our team of experts will work with you to set up the relevant tooling and procedures tailored to your organization's unique needs, ensuring that you are readily protected and prepared to respond.
Beyond Antivirus
While antivirus (AV) solutions are designed to detect and block known threats, they can't keep up with the constantly evolving threat landscape of today's cyberattacks. Unlike a general AV, our service provides continuous monitoring of not only your devices, but also your network, user and system behavior, while reporting suspicious interactions.
Ready to Respond
The solution is designed to respond to security incidents that occur on and between endpoints, such as laptops, desktops, servers, cloud environments and mobile devices on all major operating systems and with large cloud providers. The response aspect of our MDR solution involves taking immediate action to contain incidents and interact with infected systems. This may involve the isolation of endpoints, pulling evidence or artifacts from endpoints, and deploying new rules or triggers to hunt for the adversary.
If you choose to have your networks and systems monitored 24/7 for cyber threats and attacks through a Security Monitoring Service, you benefit from the expertise and deep experience of our team. We rely on cutting-edge XDR technologies that enable effective and comprehensive monitoring.
Discover which three Microsoft security products are essential for this setup—and how they actively contribute to securing your IT environment: The Essentials for Effective Security Monitoring
Minimize Damage
The goal of the response phase is to minimize the impact of the incident and prevent it from spreading to other endpoints or systems within the organization's network. By having a strong response capability in place, organizations can improve their security posture and reduce the risk of cyberattacks causing significant damage.
On-site Intervention 24/7
Our MDR customers can rely on years of expertise in reacting to incidents and suspicious activities, providing prompt and effective responses. Our expertise ensures immediate measures are put in place, industry standards are followed, and the entire fleet is thoroughly investigated. Our team is available around the clock to jump on business-critical events. Remote and on-site. Thus, our digital forensics and incident response service (DFIR service) is an integral part of the managed detection and response offering.
Expertise on Call
With dedicated access to our MDR and DFIR hotline, you get direct access to a panel of experts without going through a call center. Security-relevant questions, decisions and actions can be backed up and challenged with the help of our cyber security specialist team. You will receive competent recommendations and suggestions that will help you move forward.
Annual Security Benchmark
We defend your business as if it were our own and help you make the most of your Microsoft subscription security features. We will guide you to get the important things right. The yearly benchmark will point out crucial steps to maintain and improve resilience against cyberattacks.
6 Good Reasons to Choose Compass Security for Your Security Monitoring
As ethical hackers (penetration testers), we have been simulating targeted attacks on IT infrastructures for more than 25 years. As a result, we're intimately familiar with the methods and tricks of cybercriminals. We also use our experience from red teaming and incident response to improve monitoring and continuously adapt the detection strategy. This ensures a fast and effective response to cyber threats, which can reduce or even prevent follow-up costs.
Specifically, this means minimizing
- business interruption,
- disclosure of operational and business information
- reputational damage or
- financial loss due to fraud.
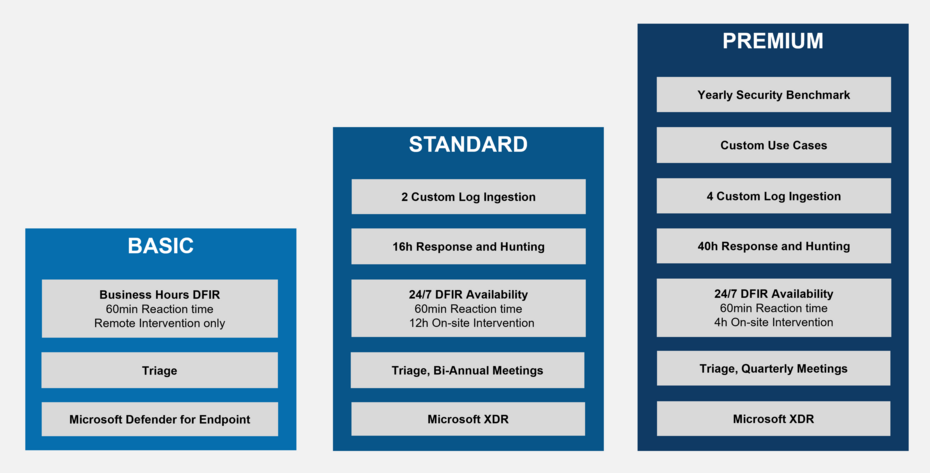
Small and mid-sized businesses often lack the human and technical resources to effectively monitor their IT systems. Even mid-sized organizations with more complex infrastructures rarely have sufficient resources for 24/7 monitoring.
This is where our contract models come in: They are tailored to the needs of SMEs. Micro-businesses often choose our basic services, which are derived from the number of endpoints. SMEs can also opt for a more comprehensive subscription model which bundles optional services in attractive packages.
Cybersecurity doesn't have to be all-encompassing from the start. We meet you where your organization is and can grow with you.
The service can be rolled out for a small group of users and then scaled and adapted as your organization's needs and circumstances change. The Microsoft cloud platform reduces initial installation time to a matter of hours. We help you get the most out of your paid licenses.
Compass Security sets up security monitoring in the customer's Microsoft tenant environment. We hand over all rule sets and automations to you. These will be installed and maintained within a subscription relating to your tenant. We centrally manage updates and changes so that all customers benefit from new features.
You remain in control at all times by giving us the authority to monitor or revoke it if necessary, for example to transfer the services to some other service provider.
Cyberattacks happen 24/7. Thanks to our established on-call organization, our specialists are available around the clock to take immediate action in the event of a cyber emergency to counter attacks before they spread. We can help you manage and investigate incidents, meet breach reporting requirements, and provide crisis communications templates.
Our goal is to minimize the actual damage and protect your company's reputation.
We are ethical hackers with a strong customer focus. A common understanding of the circumstances and requirements is the basis for a great cooperation. We value direct communication and a strong and trustful relationship between parties.
We are hungry for knowledge and use our experience and technical skills to offer you added value.
Hear directly from our customers about their experience with our services: Testimonials
We are glad to answer your questions personally: Your contact person